
Three-quarters of Czech employees have not yet had the experience of their computer, smartphone, or online account being hacked, but this does not mean that this will not happen tomorrow. In just one moment, they can lose their data and their personal identity and fall victim to webcam snooping and eavesdropping, which can ultimately lead to compromising their employer’s corporate IT infrastructure. Viewers of Promlčeno (Time-barred), which will screen at Czech cinemas from 28 April 2022, can see for themselves how an attacked device can be exploited. The movie realistically shows what neglecting cyber security can lead to.
Ipsos – a partner and expert adviser of the makers of Promlčeno – conducted an exclusive survey for Soitron to find out how careful employees are when using their business mobiles, tablets, and computers; what their attitude is to online security; and what experience they have with hacking. The survey was conducted on a sample of 1050 respondents aged from eighteen to sixty-five.
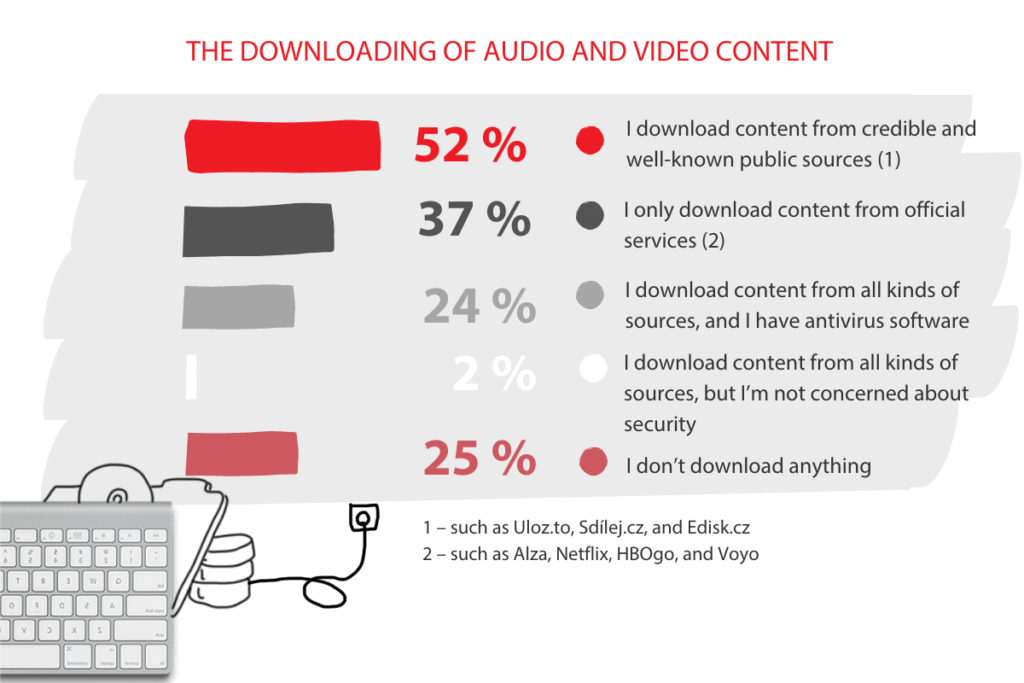
The survey shows that up to 52% of users download content from file-sharing platforms such as Uloz.to, Sdílej.cz, and Edisk.cz. Another 37% of users download content only from official services (e.g. Alza, Netflix, HBOgo, and Voyo). Twenty-four percent of users download from all kinds of sources, but their devices are protected by antivirus software. Two percent of users don’t care about security at all when downloading files. “It is only 2%. But in absolute numbers, this is an alarmingly large group of Czech employees who download data from anywhere without ever thinking about security,” warns Michal Novák, the technical director of Soitron.
From the security point of view, it does not really matter what people use to download content. As many as 64% of users behave the same on computers and mobile devices, 20% of them reported that they behaved more cautiously on mobile devices, and 17% of respondents claimed to be more cautious on their computers. When we looked at whether companies made an effort to educate their employees about cybersecurity, we found that 66% of employees had been trained by their employers on how to use and behave safely in the corporate network. Cybersecurity awareness seems to grow with age. “Although two-thirds of Czech employees receive training, it is important to realize that there are still a large number of people who do not know how to behave within the corporate network or how to properly handle their allocated devices and corporate accounts. Another question is how effective the training actually is,” argues Novák
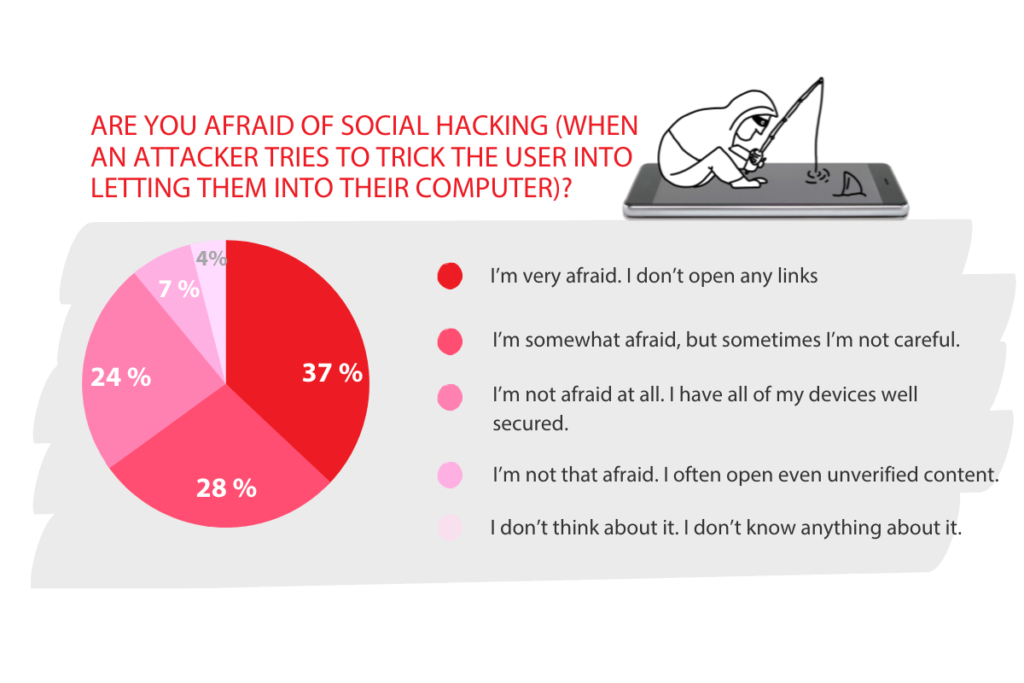
Thirty-seven percent of survey participants reported fearing social hacking, i.e. the theft of their digital identity through social engineering. That’s why they don’t open any links, they don’t install any unverified software, and they worry that they might be tricked into downloading something dangerous. Older employees in particular are afraid of being hacked, and concern clearly grows with age. In the event of a successful attack, only a very small proportion of users (10%) would be willing to pay something to an attacker who had stolen their private data or photos. Younger people tended to be more willing to pay at least a small amount.
Cyberattacks on IT infrastructures can cause serious concerns for organizations. And it doesn’t matter if it’s an industrial company or a law firm, as the viewers of Promlčeno shall learn. Karel Roden, starring in the movie in the role of an IT specialist, successfully attacks the computer network of a law firm. This is the basis for a thrilling story.
Successful hacking into industrial plant systems can lead to shutting down an assembly line. The resulting damage caused by such an event may add up to hundreds of millions of Czech crowns, depending on the length of the production downtime. Non-manufacturing companies are not much better off. Even they can be severely affected and largely paralysed. And it does not take much to compromise an organization’s integrity. “An unsuspecting employee can fall victim to phishing or an infected attachment sent to them by email. In this way, the attacker can steal the employee’s personal identity and with that get access to the corporate infrastructure and even gain control to the point where he can do whatever he wants with the systems, including stealing stored data and even controlling devices connected to the corporate network,”adds Novák. This is exactly what Promlčeno shows.
We are in the process of finalizing. If you want to be redirected to our old version of web site, please click here.